We've built a platform that should make it easy to describe your API, create rules and roles, and know that your data is both available to who needs it, and locked up tight from who shouldn't be touching it.
When you build your API there are basically two things to configure:
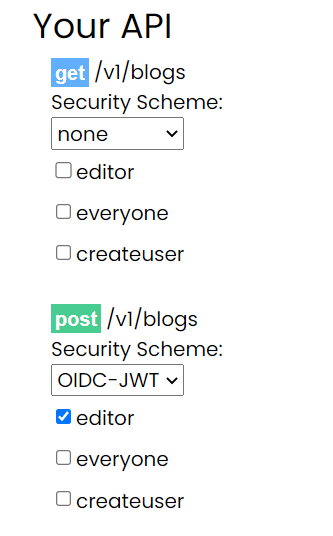
Do you want to apply security?
While data security is always critical, in real life it turns out that not every API endpoint needs to be secure. By default we enable OIDC-JWT, which will require the consumer to have a valid token, but you can also toggle that to "none" if you are willing to allow unfettered, anonymous access to your data.
What roles are needed to access this?
If the endpoint requires security you can decide what roles that use has to have in order to access this endpoint. You can customize the roles in our admin panel (or over our API), but we have a few reserved words:
- everyone: the 'everyone' attribute is given to, well, everyone who has an account. By default we allow access to everything by everyone
- admin: The admin role may be assigned to you to help manage UXAPI services such as who gets to assign roles to users
Attribute-Based Access Control (ABAC)
We allow you to define unique IDs for consumers of your API to apply Attribute-Based Access Control to assign ownership to a specific object or collection based on a variable in the path.
For example, all the blogs in the /v1/blogs collection have a unique identifier (a UUID), and if we wanted to grant ownership of specific blogs we might include a list of those IDs in our authentication.
PUT /v1/blogs/1eecea64-b936-460c-be4f-fec4d4861ed5
Replace the contents of this single object
Requires theeditorrole and the blogId 1eecea64-b936-460c-be4f-fec4d4861ed5 in claims
Now as the editor creates new blog posts, we can automate a list of which ones they get to edit. That is, just because I can edit and delete my own blogs, doesn't mean I should be able edit and delete your blogs, even if they are in the same collection.
Managing Users
As part of the platform we include a "users service" so you can add people and services to your API and manage their roles. Currently this is done using the core API service with these services:
- Users Service: Create, review and update users.
- Users Claims: Manage the user's roles and attributes
- Token Service: Generate OIDC tokens based on user credentials that are used in your API
